How to Build Internet's Hospital
 The Treachery of Images — René Magritte
The Treachery of Images — René Magritte
N.B: This paper is not an InfoSec research article, a history/symbolism essay or an official statement from Yogosha.
It should only be considered as a “Spontaneous Prose”* *of an ongoing journey, about building a bridge between InfoSec and DevOps industries through #SE, #Cloud, #OpenSource and #BugBounty. After all, it’s only full of open-source ideas shared in CC BY-NC 3.0.
Excuse my French, Kudos for challenging.
**TL;DR: **We need Hackers in the loop to Heal the cancer that is killing /b/.
But in capitalist reality, as distinguished from its textbook picture, it is not (price) competition which counts but the competition from the new commodity, the new technology, the source of supply, the new type of organization […] Competition which […] strikes not at the margins […] of the existing firms but as their foundations and their very lives. Joseph A. Schumpeter in Capitalism, Socialism and Democracy, 1942
Thoughts of a Doctor’s son

I had many nicknames in my life, but the first and founding one was “ولد الطبيب” (~ Doctor’s son), a kinda “social golden key” in Morocco. This “dom0” nickname learned what empathy, compassion and dedication means directly from the source. From someone that sworn Hippocratic’s oath, spends relentless hours on practice/phone to treat children with intellectual disability or other developmental conditions, but nevertheless finds time to read books.
The reading of all good books is like a conversation with the finest minds of past centuries. — René Descartes
I spent my childhood between a keyboard and a bookshelf. Between “cyber” e-zines and books, where Dostoyevsky’s existentialism confronts TAZ’s anarchism, and where Madchat follows the steps of Al-Khalil ibn Ahmad al-Farahidi.
This childish habit saved me during the last “c’est la meeerde” death valley. Not only as an inspiration source, but also a great mean to sharpen critical thinking. Three books stood out, and were great lighthouses in this ocean of chaos that we call “Information” age.
The first one is "Ces histoires insolites qui ont fait la médecine" (~ The unusual stories that made Medicine) where Prof. Fabiani shares with the reader a glimpse of his history courses in Paris V.
Did you know, for instance, that Socrate last words — I owe the sacrifice of a rooster to Asklepios — were an inspiration for Hippocrates deontology? Or that the École de Chirurgie was built & founded due to a fistula in Louis XIV’s ass? Or that Semmelweis, the “savior of mothers” who gave birth to Evidence-based medicine, died of an infection after being severely beaten by several guards in a mental institution? He was considered mad because he asked physicians to wash their hands between an autopsy and a childbirth to reduce childbed fever.
But the true essence of this book is in its last page, that quickly reads:
[…] Science history is somehow different from History, because it has this unique thread, this unavoidable goal that is scientific truth. And this truth is unique, even if different ways to get a glimpse of it exists. It is then possible to find out some “big picture” patterns. Maybe then we can take some lessons out of it, some critical thinking about our behaviors and errors. Alluding it was the aim of this book. Concerning the future of medicine, I know only one way to predict it, it is to create it…

These patterns are worded as “Life cycles” in the second book — The Master Switch — where Tim Wu strategically analyzed the rise and fall of past and present information empires.
I’ll just leave those 2 elements here without comments…
@dakami I’ve come to the realization that Web security is predominately a kind of janitorial work. @Hi_T_ch @ErrataRob @BrendanEich
— Jeremiah Grossman (@jeremiahg) March 10, 2016

… Or maybe add one more wishful thinking: Is it possible to stop these “vulgar” websites from being produced in the first place? Or in other words, can we, as Internet’s doctors, do prevention in this mess we call Digital Information Security?

#FrenchDoItBetter
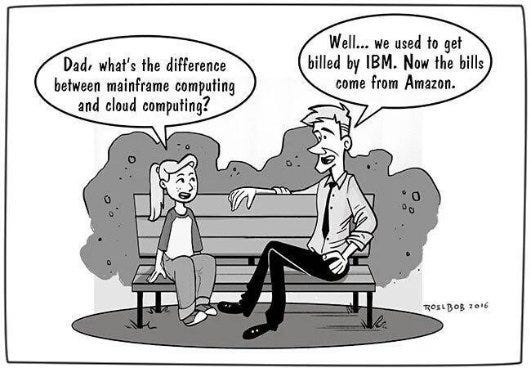
What if I told you that the ~70 registered websites every minute could be “cloud ready” and “security tested” before going live, only by the price of 3 additional files in the git folder?

Let me KISS it for you: Imagine your webapp in a Web Operation Room, having in hand those 3 files.
-
A Makefile, because you know, we’ve all man that. It’s back on DevOps track, and became an elegant way to keep things clean.
-
A Dockerfile (or config.json when OCI’s OCF will be adopted) as an “Application Bundle Builders”, aka “give me all your dependencies in one file and I’ll pop a VM/container for you”.
-
A Jenkinsfile to define CI’s multibranch workflows, and because J2EE.
Your webapp, in a continuous delivery system, will get all the treatment needed ranging from a CT scan for preliminary bug identification, to Clinicians if it needs refining before going live.
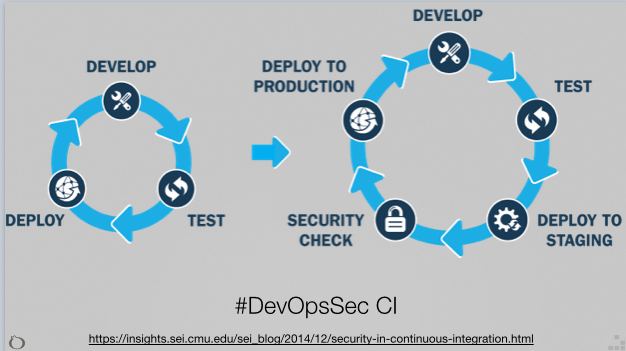
The whole point of this DevOpsSec approach is to give agility to InfoSec by being as close as possible to Dev and Ops code, and by rediscovering communication between Makers, Builders, and Healers.
In InfoSec reality, this DevOpsSec approach have 3 immediate effects:
-
Pair-Programing: By pushing issues directly to the project tracking software and interact on it. Devs will not only be proficient for correcting it, but will be security aware in situ/in prod, not in a 3 days vanilla security course.
-
The ability to outsource “security test risks”. Wanna a quick health check for your webapp? Just pop a clean staging image somewhere in “the Cloud”, and give the IP address to your nearest Bug Bounty platform. Even if Hunters finds out some critical vuln, it won’t have operational impact if the testing machines are kept isolated.
-
As a bonus, Infrastructure as Code possibilities are a good way out for a “Patch once, Deploy at once” strategy that will ease Blue team work, or for a “pre-rolled and compliant” deployment strategy that will give better visibility for Audit & Compliance teams.
We, as in Yogosha, spent the last months testing those wishful hypothesis. We had, for instance, this great opportunity to meet the security group of Guide Share France, member of GSE last March.
We’ve been honored to share a meal, to be challenged and to build bridges all evening with those who have already seen it all.
We received this email the following day:
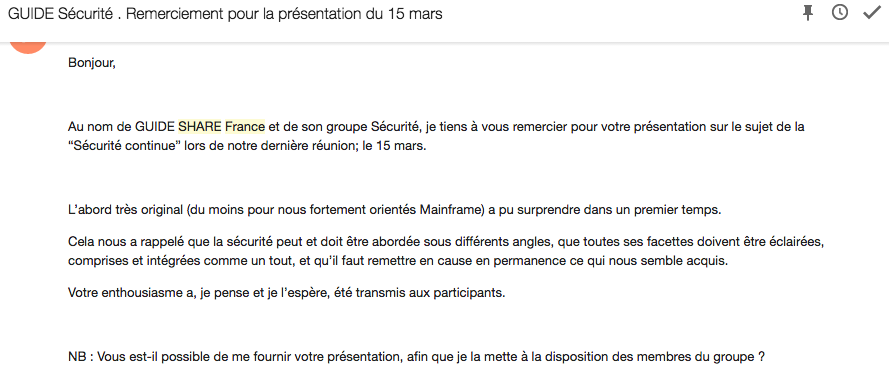
[…]This original approach (for us Mainframe users) was surprising at first. But it reminded us that Security could and should be observed by different angles, that all of its parts should be enlightened, understood and integrated as a whole, and finally that we need to continuously question what we take for granted.[…] — GSF
Those kind words from those wise people ringed a bell. A bell in Pr. Fabiani’s book epigraph, citing Emile Littré.

Medicine Science, if it don’t want to get belittled as a job, should take care of it’s history, and heal the old monument that time has bequeathed— Emile Littré 1829
The Art of Trolling

We’re living exceptional times, where technology is eating the world, even personified as a “Cyberpower”.
Andrew S. Grove describes this *“something changed” *period as a Strategic Inflection Point, or “what happens to a business when a major change takes place in its competitive environment. A major change due to introduction of new technologies”, like what happened not so long ago.
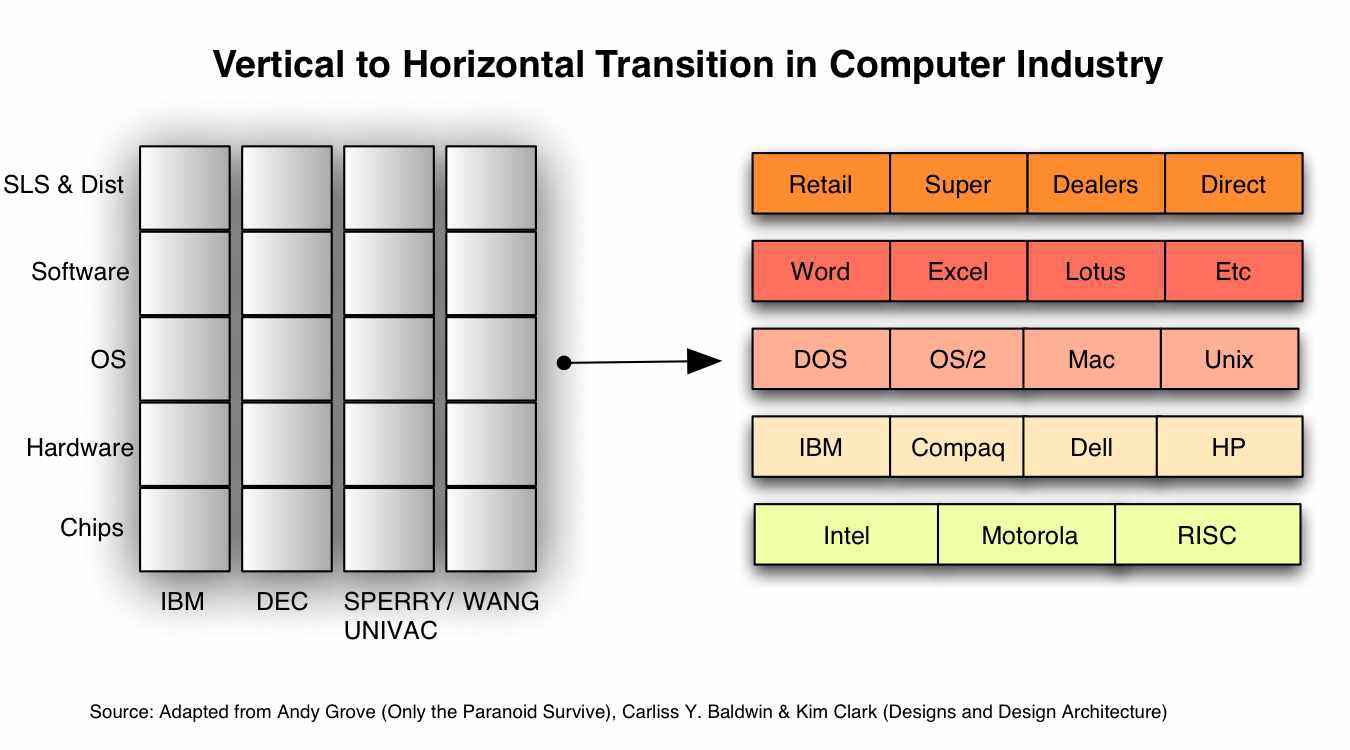
Maybe that today, we have the technology to start building this abstract decentralized hospital,
Maybe that we are on the edge of another programing paradigm, a kind of Neural Oriented Programing,
Maybe Europe is pinging back and will eventually do what it does, diplomacy and regulation,
But I’m sure of one thing. Oui nide iou to build this hospital.
To run:
$ docker run -d -p 9001:9001 --restart=always -t jess/tor-relay
« Il vaut mieux rêver sa vie que la vivre, encore que la vivre, ce soit encore la rêver. » Marcel Proust